Новини світу мікро- та наноелектроніки
NUBURU provides year-end update regarding strategic milestones
My first project iR sensitive circuit
 | submitted by /u/Life-Name3309 [link] [comments] |
Where co-packaged optics (CPO) technology stands in 2026

Co-packaged optics (CPO) technology, a key enabler for next-generation data center architectures, promises unprecedented bandwidth density and power efficiency by tightly integrating optical engines with switch silicon. But after nearly a decade of existence, where does this next-generation optical interconnect technology stand in terms of broad commercial realization?
But before we delve into CPO’s technology roadmap and its future deployment prospects, here is a brief introduction to this silicon photonics architecture and how it empowers artificial intelligence (AI), high-performance computing (HPC), and high-speed networking applications where electrical signaling over copper wires is reaching its limits.

Figure 1 CPO integrates optical transceivers directly with switch ASICs or processors to enable low-power, high-bandwidth links. Source: Broadcom
CPO, which integrates optical components directly into a single package, minimizes the electrical path length, significantly reducing signal loss, enhancing high-speed signal integrity, and containing latency. In other words, CPO enhances data throughput by leveraging high-bandwidth optical engines that deliver higher data transfer rates and are less susceptible to electromagnetic interference (EMI) than traditional copper connections.
Moreover, this silicon-photonics integration improves power efficiency by reducing the need for high-power electrical drivers, repeaters, and retimers. Case in point: by shortening the copper trace, CPO could improve the link budget enough to remove digital signal processor (DSP) or retimer functionality. That significantly reduces the overall power per bit, a key metric in AI data center management.
Below is a sneak peek at major CPO activities during 2025; it offers a glimpse of product launches and the actual readiness of CPO’s basic building blocks.
CPO’s 2025 progress report
In January 2025, Marvell announced advances in its custom XPU architecture integrated with CPO technology. The company showcased how its custom AI accelerator architecture combines XPU compute silicon, HBM, and other chiplets with its 3D SiPho engines on the same substrate using high-speed SerDes, die-to-die interfaces, and advanced packaging technologies.
That eliminates the need for electrical signals to leave the XPU package into copper cables or across a PCB. Furthermore, connections between XPUs can achieve faster data transfer rates and distances that are 100x longer than electrical cabling. Marvell’s 3D SiPho engine supports 200 Gbps electrical and optical interfaces.

Figure 2 XPU with integrated CPO enhances AI server performance by increasing XPU density from tens within a rack to hundreds across multiple racks. Source: Marvell
“AI scale-up servers require connectivity with higher signaling speeds and longer distances to support unprecedented XPU cluster sizes,” said Nick Kucharewski, senior VP and GM of the Network Switching Business Unit at Marvell. “Integrating co-packaged optics into custom XPUs is the logical next step to scale performance with higher interconnect bandwidths and longer reach.”
Four months later, in May 2025, Broadcom offered a glimpse of its third-generation 200G per lane CPO technology. The company’s CPO journey began in 2021 with the Tomahawk 4-Humboldt chipset, and the second-generation Tomahawk 5-Bailly chipset became the industry’s first volume-production CPO solution.
“Broadcom has spent years perfecting our CPO platform solutions, as evidenced by the maturity of our second-generation 100G/lane products and the ecosystem readiness,” said Near Margalit, VP and GM of the Optical Systems Division at Broadcom. The company also claims that, in addition to edge switch ASICs and optical-engine technology, it offers a comprehensive ecosystem of passive optical components, interconnects, and system solutions partners.

Figure 3 CPO offers a sustainable path forward by addressing the power constraints and physical limitations of traditional pluggable optics. Source: Broadcom
In October 2025, Broadcom claimed that Meta has tested its CPO solutions for one million link hours without a single link flap in a high-temperature lab characterization environment. A link flap is a brief connectivity disruption; it’s a critical reliability metric in high-performance data center networks.
Besides CPO heavyweights like Broadcom and Marvell, there are notable startups in the silicon photonics realm, striving to overcome electrical I/O bottlenecks. For instance, Ayar Labs, a supplier of optical interconnect solutions, has incorporated its TeraPHY optical engines into ASIC design services of Global Unichip Corp. (GUC), a Hsinchu, Taiwan-based chip developer.
In November 2025, Ayar Labs announced that it has integrated its optical engines into GUC’s advanced packaging and ASIC workflow, a critical step toward future CPO deployment. The joint design effort helps address key challenges of CPO integration: architectural, power and signal integrity, mechanical, and thermal.

Figure 4 In this CPO, two TeraPHY optical engine chiplets (left) are shown with a customer FPGA (center) within the same SoC package. Source: Ayar Labs
“The future of AI and data center scale-up will not be possible without optics to overcome the electrical I/O bottleneck,” said Vladimir Stojanovic, CTO and co-founder of Ayar Labs. “Working with GUC on advanced packaging and silicon technologies is an important step in demonstrating how our optical engines can accelerate the implementation of co-packaged optics for hyperscalers and AI scale-up.”
CPO in 2026 and beyond
While CPO proponents are eager to claim that the CPO revolution is at our doorstep, industry watchers like Yole Group see large-scale deployments between 2028 and 2030. Meanwhile, pluggable modules—inserted into the front panel of a switch sitting at the edge of the PCB—will remain competitive.
Market research firm LightCounting also predicts that optical modules will continue to account for the majority of optical links in data centers throughout the decade. At the same time, however, optical transceiver technology will continue to steadily shift toward placing the optics closer to the ASIC.
That’s because traditional pluggable optical modules are increasingly constrained by signal loss, power consumption, and latency due to long electrical traces between the switch ASIC and the optical engine. CPO overcomes these limitations by placing the optical engine much closer to the switching silicon.
The migration of the optical engine closer to the switch ASIC shortens the length of copper trace used for electrical signalling, thereby improving electrical performance. However, the seamless attachment of optical engines to switch ASICs or XPUs requires a range of packaging approaches, including 2.5D interposers, through-silicon vias (TSVs), fan-out wafer-level packaging, and 3D integration enabled by hybrid bonding.
These advanced packaging technologies are steadily evolving, and so is CPO deployment. IDTechEx projects that the CPO market will exceed $20 billion by 2036, growing at a robust CAGR of 37% from 2026 to 2036.
Related Content
- The Rise of Co-Packaged Optics
- AI Clusters Spur Optical Connectivity
- The advent of co-packaged optics (CPO) in 2025
- Global Insights into the Co-Packaged Optics Technology Platform
- AI Performance Now Depends on Optics (and CPO is the Front Line)
The post Where co-packaged optics (CPO) technology stands in 2026 appeared first on EDN.
Guard circuit provides impedance matching

The first hits from a Google search of the term “guard circuit” produce a series of references to the National Guard on some security circuit. Deep in the list is a printed circuit board company that touts that they design guard rings on critical circuits. So just what are they?
Wow the engineering world with your unique design: Design Ideas Submission Guide
Guard circuitAnalog Devices references guard shields around their op amps as well as the printed circuit traces [1]. These traces are called guard rings; they circle and shield critical circuits. Another well-known reference on electromagnetic interference (EMI) discusses guard shields in the early edition [2]. The use of op amp shields, together with shielded pairs, and grounded so as to eliminate differential input noise. This is accomplished by connecting the cable shield to the op amp shield. Another section discusses guarded meters.
In this example, the recommended connection should be made so as not to cause current flow through any measuring leads. The term “guard shield” is missing from the author’s subsequent book on the same topic [3].
High-power active devices can use guard shields, in the form of a thin conductive strip placed between two electrical insulating yet thermal conductive gaskets, used to mount the device to a heat sink [4]. The guard shield is returned to the circuit common. This results in lower leakage capacitance between the device case and the heat sink, and lower parasitic currents.
Active circuit guard wiring techniquesGuarding can be done using active circuit devices such as an operational amplifier, as shown in Figure 1. The amplifier is wired as a coupler or isolator; the feedback is between the output and the positive input. The coaxial shield is connected to that output, which is the active shield, a low impedance source equal to the input voltage. A large leakage resistor is shown to complete the Spice simulation. The center wire is connected to the measured devices or circuit.
 Figure 1 An active circuit guarding with op amps wired as a coupler or isolator and the feedback is between the output and positive input.
Figure 1 An active circuit guarding with op amps wired as a coupler or isolator and the feedback is between the output and positive input.
Another possible application for the guard technique is interfacing a pulse signal. A pulse signal’s Fourier transform has a fundamental and odd harmonics. For high-frequency signal transmission, twisted pairs such as Cat 5 are frequently used. The source and load impedance should be equal to prevent reflections. But what if this is not the case? If a guarded circuit is used, the source is connected to the operational amplifier input, which has a high input impedance, and the wire is guarded from the return path.
An example where this circuit could be employed is interfacing industrial or process fluid flow meters. A variety of meters, such as positive displacement, which uses oval gears, and a pickup circuit to count revolutions. This includes turbine meters, which have blades internal to the meter and rotate proportionally to the flow rate.
The vortex flow meter is based on the Von Karman effect. As the fluid flows around a fixed body or blunt object, vorticity is shed alternately. The frequency of this vortex shedding is proportional to the fluid velocity. This signal can be sensed in several ways and is a pulse signal.
The Coriolis mass flow meters make use of two vibrating tubes. Flow through the tubes causes Coriolis forces to twist the tubes, resulting in a phase shift. The time difference between the waves is measured and is directly proportional to the mass flow rate.
All these meters have a calibration factor or K, which is a constant relating to the calibration, for example, K= 800 pulses per gallon. The pulses, electrical circuits, and internal resistances can vary depending on the meter. There are a variety of signal levels as well as input and output resistances between these meters and the input circuit cards.
A frequent application for these meters is to charge a known fluid volume in a tank. An accurate method is to count up or down pulses in an industrial controller. It is more accurate to measure the signal as a pulse, adding interface circuitry such as an analog flow rate signal, and integrating that signal will be subject to circuit inaccuracies and, assuming the operation is done in an industrial controller, be subject to scan sampling errors.

Figure 2 Active circuit guarding, pulse interface circuit based on 200 feet RG-58 coax cable with distributed capacitance and resistance.
Test circuitThis proposed circuit was tested based on a pulse waveform based on a typical meter as discussed. The pulse assumed is 1-ms wide with a 3-ms period. The pulse is generated by a LMC555 wired in astable operation with a 1-kΩ pull up load to a 5-V supply.
The isolation operational amplifier is 1/4 LM324 wired such that the output is a non inverting unity amplifier. The guard circuit is a 40 foot RG-58 coaxial cable. The amplifier is powered by its own 9-V battery. The only connection between both supplies is the single conductor wire parallel to the coax.
The results are shown in Figure 3, the circuit was able to provide an output the same as the input, and able to interface with any input impedance.

Figure 3 Pulse waveforms where yellow is the output and green is the input.
These waveforms agreed with the Spice simulation. The output closely followed the input.
Note the output waveform when expanded time scale when rising. The rapid increase followed by a ramp to the steady state is because the op amp has a very high gain, and is charging based on its supply voltage. However when the outer coax is charged to a point below the steady state output, the RC equivalent circuit is still charging expecting that the steady state at supply voltage. However when input difference is zero, the ramp ceases.

Figure 4 The pulse waveforms where yellow is the output and green is the input. The time scale 1/100 the previous figure (Figure 3).
Because almost all these flow signal transmitters have isolated electronics, the third wire, signal common, may be the same wire as the power supply return. This supply power is typically supplied from the pulse sensing electronics.
If so, that conductive path or reference is already available, usually in the same pair as the supply wire, in the form of a twisted, shielded cable. This provides magnetic and electric field EMI protection. The user only needs to provide the coaxial cable to the flow meter.
More than a shieldA guard shield is more than just a shield, either a solid conductive surface or braided cylinder, it is in concert with thoughtful wiring techniques to both active and passive components that result in mitigating EMI.
Related Content
- Power Supply Guard Circuit
- Telephone Guard Circuit
- Understanding grounding, shielding, and guarding in high-impedance applications
- Analog layout: Why wells, taps, and guard rings are crucial
References
- Sheingold, Daniel H., Transducer Interfacing Handbook, Analog Devices, Inc., Norwood, MA., 1980.
- Ott, H. W., Noise Reduction Techniques in Electronic Systems, John Wiley & Sons, New York, New York, 1988.
- Ott, H. W., Electromagnetic Compatibility Engineering, John Wiley & Sons, New York, New York, 2009.
- Morrison, R., Grounding and Shielding Circuits and Interference, fifth edition, IEEE Press, John Wiley & Sons, New York, New York, 2007.
Bob Heider worked as an electrical and controls engineer for a large chemical company for over 30 years. This was followed by several years in academic and research roles with Washington University, St. Louis, MO. He is continuing to work part-time as well as mentor some student groups.
The post Guard circuit provides impedance matching appeared first on EDN.
AXT prices public offering of stock to raise $87m
Don't know what I'm doing but it worked after I was done with it :)
 | I've been buying stuff from thrift stores to learn more about electronics. I took this apart and found it had a broken circuit board. It took a couple hours and it's not pretty but it works! [link] [comments] |
EEVblog 1726 - REPAIR of an EV Charger (Unusual Twist!)
Move2Thz project targets sustainable InP-on-silicon platform and European ecosystem upscaling to mass market sub-THz applications
2026: A technology forecast for AI’s ever-evolving bag of tricks

Read on for our intrepid engineer’s latest set of predictions for the year(s) to come.
As has been the case the last couple of years, we’re once again flip-flopping what might otherwise seemingly be the logical ordering of this and its companion 2025 look-back piece. I’m writing this 2026 look-ahead for December publication, with the 2025 revisit to follow, targeting a January 2026 EDN unveil. While a lot can happen between now and the end of 2025, potentially affecting my 2026 forecasting in the process, this reordering also means that my 2025 retrospective will be more comprehensive than might otherwise be the case.
Without any further ado, and as usual, ordered solely in the cadence in which they initially came out of my cranium…
AI-based engineeringLikely unsurprisingly, as will also be the case with the subsequent 2025 retrospective-to-come, AI-related topics dominate my forecast of the year(s) to come. Take “vibe coding”, which entered the engineering and broader public vernacular only in February and quickly caught fire. Here’s Wikipedia’s introduction to the associated article on the subject:
Vibe coding is an artificial intelligence-assisted software development technique popularized by Andrej Karpathy in February 2025. The term was listed on the Merriam-Webster website the following month as a “slang & trending” term. It was named Collins Dictionary‘s Word of the Year for 2025.
Vibe coding describes a chatbot-based approach to creating software where the developer describes a project or task to a large language model (LLM), which generates code based on the prompt. The developer does not review or edit the code, but solely uses tools and execution results to evaluate it and asks the LLM for improvements. Unlike traditional AI-assisted coding or pair programming, the human developer avoids examination of the code, accepts AI-suggested completions without human review, and focuses more on iterative experimentation than code correctness or structure.
Sounds great, at least in theory, right? Just tell the vibe coding service and underlying AI model what you need your software project to do; it’ll as-needed pull together the necessary code snippets from both open-source and company-proprietary repositories all by itself. If you’re already a software engineer, it enables you to crank out more code even quicker and easier than before.
And if you’re a software or higher-level corporate manager, you might even be able to lay off (or at least pay grade-downscale) some of those engineers in the process. Therein explaining the rapid rollout of vibe coding capabilities from both startups and established AI companies, along with evaluations and initial deployments that’ll undoubtedly expand dramatically in the coming year (and beyond). What could go wrong? Well…
Advocates of vibe coding say that it allows even amateur programmers to produce software without the extensive training and skills required for software engineering. Critics point out a lack of accountability, maintainability, and the increased risk of introducing security vulnerabilities in the resulting software.
Specifically, a growing number of companies are reportedly discovering that any upfront time-to-results benefits incurred by AI-generated code end up being counterbalanced by the need to then reactively weed out resulting bugs, such as those generated by hallucinated routines when the vibe coding service can’t find relevant pre-existing examples (assuming the platform hasn’t just flat-out deleted its work, that is).
To that point, I’ll note that vibe coding, wherein not reviewing the resultant software line-by-line is celebrated, is an extreme variant of the more general AI-assisted programming technology category.
But even if a human being combs through the resultant code instead of just compiling and running it to see what comes out the other end, there’s still no guarantee that the coding-assistance service won’t have tapped into buggy, out-of-date software repositories, for example. And there’s always also the inevitable edge and corner cases that won’t be comprehended upfront by programmers relying on AI engines instead of their own noggins.
That all said, AI-based programming is already having a negative impact on both the job prospects for university students in the computer science curriculum and the degree-selection and pursuit aspirations of those preparing to go to college, not to mention (as already alluded to) the ongoing employment fortunes of programmers already in the job market.
And for those of you who are instead focused on hardware, whether that be chip- or board-level design, don’t be smug. There’s a fundamental reason, after all, why a few hours before I started writing this section, NVIDIA announced a $2B investment in EDA toolset and IP provider Synopsys.
Leveraging AI to generate optimized routing layouts for the chips on a PCB or the functional blocks on an IC is one thing; conventional algorithms have already been handling this for a long time. But relying on AI to do the whole design? Call me cynical…but only cautiously so.
Memory (and associated system) supply and pricesSpeaking of timely announcements, within minutes prior to starting to write this section (which, to be clear, was also already planned), I saw news that Micron Technology was phasing out its nearly 30-year old Crucial consumer memory brand so that it could redirect its not-unlimited fabrication capacity toward more lucrative HBM (high bandwidth memory) devices for “cloud” AI applications.
And just yesterday (again, as I’m writing these words), a piece at Gizmodo recommended to readers: “Don’t Build a PC Right Now. Just Don’t”. What’s going on?
Capacity constraints, that’s what. Remember a few years back, when the world went into a COVID-19 lockdown, and everyone suddenly needed to equip a home office, not to mention play computer games during off-hours?
Device sales, with many of them based on DRAM, mass storage (HDDs and/or SSDs), and GPUs, shot through the roof, and these system building blocks also then went into supply constraints, all of which led to high prices and availability limits.
Well, here we go again. Only this time, the root cause isn’t a pandemic; it’s AI. In the last few years’ worth of coverage on Apple, Google, and others’ device announcements, I’ve intentionally highlighted how much DRAM each smartphone, tablet, and computer contains, because it’s a key determinant of whether (and if so, how well) it can run on-device inference.
Now translate that analogy to a cloud server (the more common inference nexus) and multiply both the required amount and performance of memory by multiple orders of magnitude to estimate the demand here. See the issue? And see why, given the choice to prioritize either edge or datacenter customers, memory suppliers will understandably choose the latter due to the much higher revenues and profits for a given capacity of HBM versus conventional-interface DRAM?
Likely unsurprising to my readers, nonvolatile memory demand increases are pacing those of their volatile memory counterparts. Here again, speed is key, so flash memory is preferable, although to the degree that the average mass storage access profile can be organized as sequential versus random, the performance differential between SSDs and lower cost-per-bit HHDs (which, mind you, are also increasingly supply-constrained by ramping demand) can be minimized.
Another traditional workaround involves beefing up the amount of DRAM—acting as a fast cache—between the mass storage and processing subsystems, although per the prior paragraph it’s a particularly unappealing option this time around.
I’ve still got spare DRAM DIMMs and M.2 SSD modules, along with motherboards, cases, PSUs, CPUs, and graphics cards, and the like sitting around, left over from my last PC-build binge.
Beginning over the upcoming holidays, I plan to fire up my iFixit toolkits and start assembling ‘em again, because the various local charities I regularly work with are clearly going to be even more desperate than usual for hardware donations.
The same goes for smartphones and the like, and not just for fiscally downtrodden folks…brace yourselves to stick with the devices you’ve already got for the next few years. I suspect this particular constraint portion of the long-standing semiconductor boom-and-bust cadence will be with us even longer than usual.
Electricity rates and environmental impactsNot a day seemingly goes by without me hearing about at least one (and usually multiple) new planned datacenter(s) for one of the big names in tech, either being built directly by that company or in partnership with others, and financed at least in part by tax breaks and other incentives from the municipalities in which they’ll be located (here’s one recent example).
And inevitably that very same day, I’ll also see public statements of worry coming from various local, state, and national government groups, along with public advocacy organizations, all concerned about the environmental and other degrading impacts of the substantial power and water needs demanded by this and other planned “cloud” facilities (ditto, ditto, and ditto).
Truth be told, I don’t entirely “get” the municipal appeal of having a massive AI server farm in one’s own back yard (and I’m not alone). Granted, there may be a short-duration uptick in local employment from construction activity.
The long-term increase in tax revenues coming from large, wealthy tech corporations is an equally enticing Siren’s Song (albeit counterbalanced by the aforementioned subsidies). And what politician can’t resist proudly touting the outcome of his or her efforts to bring Alphabet (Google)/Amazon/Apple/ Meta/Microsoft/[insert your favorite buzzy company name here] to his or her district?
Regarding environmental impacts, however, I’ll “showcase” (for lack of a better word) one particularly egregious example: Elon Musk’s xAI Colossus 1 and 2 data centers in Memphis, Tennessee.
The former, a repurposed Electrolux facility, went online in September 2024, only 122 days after construction began. The latter, for which construction started this March, is forecasted, when fully equipped, to be the “First Gigawatt Datacenter In The World”. Sounds impressive, right? Well, there’s also this, quoting from Wikipedia:
At the site of Colossus in South Memphis, the grid connection was only 8 MW, so xAI applied to temporarily set up more than a dozen gas turbines (Voltagrid’s 2.5 MW units and Solar Turbines’ 16 MW SMT-130s) which would steadily burn methane gas from a 16-inch natural gas main. However, according to advocacy groups, aerial imagery in April 2025 showed 35 gas turbines had been set up at a combined 422 MW. These turbines have been estimated to generate about “72 megawatts, which is approximately 3% of the (TVA) power grid”. According to the Southern Environmental Law Center (SELC), the higher number of gas turbines and the subsequent emissions requires xAI to have a ‘major source permit’, however, the emissions from the turbines are similar to the nearby large gas-powered utility plants.
In Memphis, xAI was able to sidestep some environmental rules in the construction of Colossus, such as operating without permits for the on-site methane gas turbines because they are “portable”. The Shelby County Health department told NPR that “it only regulates gas-burning generators if they’re in the same location for more than 364 days. In the neighborhood of South Memphis, poor air quality has given residents elevated asthma rates and lower life expectancy. A ProPublica report found that the cancer risk for those living in this area already have four times the risk of cancer than what the Environmental Protection Agency (EPA) considers to be an acceptable risk. In November 2024, the grid connection was upgraded to 150 MW, and some turbines were removed.
Along with high electricity needs, the expected water demand is over five million gallons of water per day in “… an area where arsenic pollution threatens the drinking water supply.” This is reported by the non-profit Protect Our Aquifer, a community organization founded to protect the drinking water in Memphis. While xAI has stated they plan to work with MLGW on a wastewater treatment facility and the installation of 50 megawatts of large battery storage facilities, there are currently no concrete plans in place aside from a one-page factsheet shared by MLGW.
Geothermal powerSpeaking of the environment, the other night I watched a reality-calibrating episode of The Daily Show, wherein John Stewart interviewed Elizabeth Kolbert, Pulitzer Prize-winning author and staff writer at The New Yorker:
I say “calibrating” because it forced me to confront some uncomfortable realities regarding global warming. As regular readers may already realize, either to their encouragement or chagrin, I’m an unabashed believer in the following:
- Global warming is real, already here, and further worsening over time
- Its presence and trends are directly connected to human activity, and
- Those trends won’t automatically (or even quickly) stop, far from reversing course, even if that causational human activity ceases.
What I was compelled to accept after watching Stewart and Kolbert’s conversation, augmenting my existing opinion that human beings are notoriously short-sighted in their perspectives, frequently to their detriment (both near- and long-term), were conclusions such as the following:
- Expecting humans to willingly lower (or even flatline, versus constantly striving to upgrade) their existing standards of living for the long-term good of their species and the planet they inhabit is fruitless
- And given that the United States (where I live, therefore the innate perspective) is currently the world’s largest supplier of fossil fuel—specifically, petroleum and natural gas—energy sources, powerful lobbyists and other political forces will preclude serious consideration of and responses to global warming concerns, at least in the near term.
In one sense, those in the U.S. are not alone with their heads-in-the-sand stance. Ironically, albeit intentionally, the photo I included at the beginning of the prior section was of a coal-burning power plant in China.
That said, at the same time, China is also a renewable energy leader, rapidly becoming the world’s largest implementer of both wind and solar cell technology, both of which are now cheaper than fossil fuels for new power plant builds, even after factoring out subsidies. China also manufactures the bulk of the world’s lithium-based batteries, which enable energy storage for later use whenever the sun’s not shining and the wind’s not blowing.
To that latter point, though, while solar, wind, and many other renewable energy sources, such as tidal power, have various “green” attributes both in an absolute sense and versus carbon-based alternatives, they’re inconsistent in output over time. But there’s another renewable option, geothermal power, that doesn’t suffer from this impermanence, especially in its emerging “enhanced” variety. Traditional geothermal techniques were only limited-location relevant, with consequent challenges for broader transmission of any power generated, as Wikipedia explains:
The Earth’s heat content is about 1×1019 TJ (2.8×1015 TWh). This heat naturally flows to the surface by conduction at a rate of 44.2 TW and is replenished by radioactive decay at a rate of 30 TW. These power rates are more than double humanity’s current energy consumption from primary sources, but most of this power is too diffuse (approximately 0.1 W/m2 on average) to be recoverable. The Earth’s crust effectively acts as a thick insulating blanket which must be pierced by fluid conduits (of magma, water or other) to release the heat underneath.
Electricity generation requires high-temperature resources that can only come from deep underground. The heat must be carried to the surface by fluid circulation, either through magma conduits, hot springs, hydrothermal circulation, oil wells, drilled water wells, or a combination of these. This circulation sometimes exists naturally where the crust is thin: magma conduits bring heat close to the surface, and hot springs bring the heat to the surface.
To bolster the identification of such naturally geothermal-friendly locations (the photo at the beginning of this section was taken in Iceland, for example), companies such as Zanskar are (cue irony) using AI to locate previously unknown hidden sources. I’m admittedly also pleasantly surprised that the U.S. Department of Energy just announced geothermal development funding.
And, to even more broadly deploy the technology, other startups like Fervo Energy and Quaise Energy are prototyping ultra-deep drilling techniques first pioneered with (again, cue irony) fracking to pierce the crust and get to the constant-temperature, effectively unlimited energy below it, versus relying on the aforementioned natural conduit fractures. That it can be done doesn’t necessarily mean that it can be done cost-effectively, mind you, but I for one won’t ever underestimate the power of human ingenuity.
World models (and other LLM successors)While the prior section focused on accepting the reality of ongoing AI technology adoption and evolution, suggesting one option (of several; don’t forget about nuclear fusion) for powering it in an efficient and environmentally responsible manner, this concluding chapter is in some sense a counterpoint. Each significant breakthrough to date in deep learning implementations, while on the one hand making notable improvements in accuracy and broader capabilities, has also demanded ever-beefier compute, memory, and other system resources to accomplish its objectives…all of which require more energy to power them, along with more water to remove the heat byproduct of this energy consumption. The AI breakthrough introduced in this section is no exception.
Yann LeCun, one of the “godfathers” of AI whom I’ve mentioned here at EDN numerous times before (including just one year ago), has publicly for several years now been highly critical of what he sees as the inherent AGI (artificial general intelligence) and other limitations of LLMs (large language models) and their transformer network foundations.
A recent interview with LeCun published in the Wall Street Journal echoed many of these longstanding criticisms, adding a specific call-out for world models as their likely successor. Here’s how NVIDIA defines world models, building on my earlier description of multimodel AI:
World models are neural networks that understand the dynamics of the real world, including physics and spatial properties. They can use input data, including text, image, video, and movement, to generate videos that simulate realistic physical environments. Physical AI developers use world models to generate custom synthetic data or downstream AI models for training robots and autonomous vehicles.
Granted, LeCun has no shortage of detractors, although much of the criticism I’ve seen is directed not at his ideas in and of themselves but at his claimed tendency to overemphasize his role in coming up with and developing them at the expense of other colleagues’ contributions.
And granted, too, he’s planning on departing Meta, where he’s managed Facebook’s Artificial Intelligence Research (FAIR) unit for more than a decade, for a world model-focused startup. That said, I’ll forever remember witnessing his decade-plus back live demonstration of early CNN (convolutional neural network)-based object recognition running on his presentation laptop and accelerated on a now-archaic NVIDIA graphics subsystem:
He was right then. And I’m personally betting on him again.
Happy holidays to all, and to all a good nightI wrote the following words a couple of years ago and, as was also the case last year, couldn’t think of anything better (or even different) to say this year, given my apparent constancy of emotion, thought, and resultant output. So, once agai,n with upfront apologies for the repetition, a reflection of my ongoing sentiment, not laziness:
I’ll close with a thank-you to all of you for your encouragement, candid feedback and other manifestations of support again this year, which have enabled me to once again derive an honest income from one of the most enjoyable hobbies I could imagine: playing with and writing about various tech “toys” and the foundation technologies on which they’re based. I hope that the end of 2025 finds you and yours in good health and happiness, and I wish you even more abundance in all its myriad forms in the year to come. Let there be Peace on Earth.
p.s…let me (and your fellow readers) know in the comments not only what you think of my prognostications but also what you expect to see in 2026 and beyond!
—Brian Dipert is the Principal at Sierra Media and a former technical editor at EDN Magazine, where he still regularly contributes as a freelancer.
Related Content
- 2025: A technology forecast for the year ahead
- 2024: A technology forecast for the year ahead
- 2023: A technology forecast for the year ahead
- 2022 tech themes: A look ahead
- A tech look back at 2022: We can’t go back (and why would we want to?)
- A 2021 technology retrospective: Strange days indeed
The post 2026: A technology forecast for AI’s ever-evolving bag of tricks appeared first on EDN.
Gray codes: Fundamentals and practical insights

Gray codes, also known as reflected binary codes, offer a clever way to minimize errors when digital signals transition between states. By ensuring that only one bit changes at a time, they simplify hardware design and reduce ambiguity in applications ranging from rotary encoders to error correction.
This article quickly revisits the fundamentals of Gray codes and highlights a few practical hints engineers can apply when working with them in real-world circuits.
Understanding reflected binary (Gray) code
The reflected binary code (RBC), more commonly known as Gray code after its inventor Frank Gray, is a systematic ordering of binary numbers designed in a way that each successive value differs from the previous one in only a single bit. This property makes Gray code distinct from conventional binary sequences, where multiple bits may flip simultaneously during transitions.
To illustrate, consider the decimal values 1 and 2. In standard binary, they are represented as 001 and 010, requiring two bits to change when moving from one to the other. In Gray code, however, the same values are expressed as 001 and 011, ensuring that only one bit changes during the increment. This seemingly small adjustment has significant practical implications: it reduces ambiguity and minimizes the risk of misinterpretation during state changes.
Gray codes have long been valued in engineering practice. They help suppress spurious outputs in electromechanical switches, where simultaneous bit changes could otherwise produce transient errors. In modern applications, Gray coding also supports error reduction in digital communication systems. By simplifying logic operations and constraining transitions to a single bit, Gray codes provide a robust foundation for reliable digital design.
Gray code vs. natural binary
Unlike standard binary encoding, where multiple bits may change during a numerical increment, Gray code ensures that only a single bit flips between successive values. This one-bit transition minimizes ambiguity during state changes and enables simple error detection: if more than one bit changes unexpectedly, the system can flag the data as invalid.
This property is especially useful in position encoders and digital control systems, where transient errors from simultaneous bit changes can lead to misinterpretation. The figure below compares the progression of values in natural binary and Gray code, highlighting how Gray code preserves single-bit transitions across the sequence.

Figure 1 Table compares Gray code and natural binary sequences, highlighting single-bit transitions between increments. Source: Author
When it comes to reliability in absolute encoder outputs, Gray code is the preferred choice because it prevents data errors that can arise with natural binary during state transitions. In natural binary, a sluggish system response may momentarily misinterpret a change; for instance, the transition from 0011 to 0100 could briefly appear as 0111 if multiple bits switch simultaneously. Gray code avoids this issue by ensuring that only one bit changes at a time, making the output stream inherently more reliable and easier for controllers to validate in practice.
Furthermore, converting Gray code back to natural binary is straightforward and can be done quickly on paper. Begin by writing down the Gray code sequence and copying the leftmost bit directly beneath it. Then, add this copied bit to the next Gray code bit to the right, ignoring any carries, and place the result beside the first copied digit. Continue this process step by step across the sequence until all bits have been converted. The final row represents the equivalent natural binary value.
For example, consider the Gray code 1011.
- Copy the leftmost bit → binary begins as 1.
- Next, add (XOR) the copied bit with the next Gray bit: 1 XOR 0 = 1 → binary becomes 11.
- Continue: 1 XOR 1 = 0 → binary becomes 110.
- Finally: 0 XOR 1 = 1 → binary becomes 1101.
Thus, the Gray code 1011 corresponds to the natural binary value 1101.
Gray code 1011 is not a standard weighted code, yet in a 4‑bit sequence, it corresponds to the decimal value 13. Its natural binary equivalent, 1101, also evaluates to 13, as shown below:
(1×23) + (1×22) + (0x21) + (1×20) = 8 + 4 + 0 + 1 = 13
Since both representations yield the same decimal result, the conversion is verified as correct.

Figure 2 Table demonstrates step‑by‑step conversion of Gray code 1011 into its natural binary equivalent 1101. Source: Author
Gray code output in rotary encoders
The real difference in a Gray code encoder lies in its output. Instead of returning a binary number that directly reflects the rotor’s position, the encoder produces a Gray code value.
As discussed earlier, Gray code differs fundamentally from binary: it’s not a weighted number system, where each digit consistently contributes to the overall value. Rather, it is an unweighted code designed so that only one bit changes between successive states.
In contrast, natural binary often requires multiple bits to flip simultaneously when incrementing or decrementing, which can introduce ambiguity during transitions. In extreme cases, this ambiguity may cause a controller to misinterpret the encoder’s position, leading to errors in system response. By limiting changes to a single bit, Gray code minimizes these risks and ensures more reliable state detection.
Shown below is a 4-bit Gray code output rotary encoder. As can be seen, it has four output terminals labeled 1, 2, 4, and 8, along with a Common terminal. The numbers 1-2-4-8 represent the bit positions in a 4-bit code, with each terminal corresponding to one output line of the encoder. As the rotor turns, each line switches between high and low according to the Gray code sequence, producing a unique 4-bit pattern for every position.

Figure 3 Datasnip shows terminal ID of the 25LB22-G-Z 4-bit Gray code encoder. Source: Grayhill
The Common terminal serves as the reference connection—typically ground or supply return—against which the four output signals are measured. Together, these terminals provide the complete Gray code output that can be read by a controller or logic circuit to determine the encoder’s angular position.
Sidenote: Hexadecimal output encoders
While many rotary encoders provide Gray code or binary outputs, some devices are designed to deliver signals in hexadecimal format. In these encoders, the rotor position is represented by a 4-bit binary word that maps directly to hexadecimal digits (0–F). This approach simplifies integration with digital systems that already process data in hex, such as microcontrollers or diagnostic interfaces.
Unlike Gray code, hexadecimal outputs do not guarantee single-bit transitions between states, so they are more prone to ambiguity during mechanical switching. However, they remain useful in applications where compact representation and straightforward decoding outweigh the need for transition reliability.
Microcontroller decoding of Gray code
There are several ways to decode Gray codes, but the most common way today is to feed the output bits into a microcontroller and let software handle the counting. In practice, the program reads the signals from the rotary encoder through I/O ports and first converts the Gray code into a binary value. That binary value is then translated into binary-coded decimal (BCD), which provides a convenient format for driving digital displays.
From there, the microcontroller can update a seven-segment display, LCD, or other interface to present the rotor’s position in a clear decimal form. This software-based approach not only simplifies hardware design but also offers flexibility to scale with higher-resolution encoders or integrate additional processing features.
On a personal note, my first experiment with a Gray code encoder involved decoding the outputs using hardware logic circuits rather than software.
This post has aimed to peel back a few layers of Gray codes, offering both context and clarity. Of course, there is much more to explore—and those deeper dives will come in time. For now, I invite you to share your own experiences, insights, or questions about Gray codes in the comments. Your perspectives can spark the next layer of discussion and help shape future explorations.
 T. K. Hareendran is a self-taught electronics enthusiast with a strong passion for innovative circuit design and hands-on technology. He develops both experimental and practical electronic projects, documenting and sharing his work to support fellow tinkerers and learners. Beyond the workbench, he dedicates time to technical writing and hardware evaluations to contribute meaningfully to the maker community.
T. K. Hareendran is a self-taught electronics enthusiast with a strong passion for innovative circuit design and hands-on technology. He develops both experimental and practical electronic projects, documenting and sharing his work to support fellow tinkerers and learners. Beyond the workbench, he dedicates time to technical writing and hardware evaluations to contribute meaningfully to the maker community.
Related Content
- Gray Code Fundamentals – Part 1
- Gray Code Fundamentals – Part 2
- Gray Code Fundamentals – Part 3
- Logic 101 – Part 4 – Gray Codes
- Gray Code Fundamentals – Part 5
The post Gray codes: Fundamentals and practical insights appeared first on EDN.
European firm orders two Riber MBE 6000 production systems
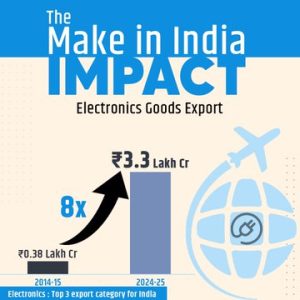
India’s Electronic Exports grow sixfold from ₹1.9 lakh crore to ₹11.3 lakh crore in a decade: Ashiwini Vaishnaw
Sh Ashwini Vaishnaw, Union Minister for Railways, Electronics, and Information Technology, took to his Twitter handle to underline India’s stride in the electronic exports. He points toward India’s ongoing transformation into a global electronics export hub driven by the sharp growth in production, jobs, and investments flowing into the sector, bolstered by various initiatives under the central government, including Make in India, PLI, ECMS, etc.
He writes, “ India’s growth story in electronics manufacturing is PM @narendramodi Ji’s vision of developing a comprehensive ecosystem.” He underlines the government’s continuity and effective oversight over the industry, which is leading to sustained development as well as growing impact on the nation and the world. The image he posted shows how the Make in India initiative has brought about a multiplication in the number of Mobile manufacturing units, from 2 in 2014-15 to 300 in 2024-25.

Electronics: Among the top 3 export categories
For India, out of the total electronics production worth Rs 11.3 Lakh crore in 2024-25, a strikingly high value of Rs 3.3 Lakh crores is attributed to exports, making electronics rank among the top 3 items exported by India. This also marks an eightfold increase in the export of the electronics item in the year 2024-25, rising from 0.38 Lakh crore in 2014-25.
Building Capacity for Modules, Equipment
He writes, “ Initial focus on finished products. Now we are building capacity for modules, components, sub-modules, raw materials, and the machines that make them.” He even goes on to add about the Electronics Component Manufacturing Scheme, wherein he talks about attracting 249 applications received amounting to ₹1.15 lakh crore investment, ₹10.34 lakh crore production, and creating 1.42 lakh jobs. He writes, “It is the highest-ever investment commitment in India’s electronics sector. This shows industry confidence.”
He also touched upon the Production-Linked Incentive (Large Scale Manufacturing-LSM), which enabled the industry to attract over ₹13,475 crore worth of investment. It is equivalent to a Production value of ~₹9.8 lakh crore. He even adds, “ Electronics manufacturing created 25 lakh jobs in the last decade. This is the real economic growth at the grassroots level. As we scale semiconductors and component manufacturing, job creation will accelerate.”
“From finished products to components, production is growing. Exports are rising. Global players are confident. Indian companies are competitive. Jobs are being created,” writes the minister as he shares India’s Make In India Impact Story.
The post India’s Electronic Exports grow sixfold from ₹1.9 lakh crore to ₹11.3 lakh crore in a decade: Ashiwini Vaishnaw appeared first on ELE Times.
Fraunhofer IAF and Max Planck Institute for Radio Astronomy provide low-noise amplifiers for ALMA radio telescope array
Micro-LED reaches make-or-break phase as first production lines ramp at AUO
Co-packaged optics market to grow at 37% CAGR to $20bn by 2036
PlayNitride to acquire Lumiode
Voltage drop across Germanium Diode (1N60) in forward bias
 | submitted by /u/SpecialistRare832 [link] [comments] |
Weekly discussion, complaint, and rant thread
Open to anything, including discussions, complaints, and rants.
Sub rules do not apply, so don't bother reporting incivility, off-topic, or spam.
Reddit-wide rules do apply.
To see the newest posts, sort the comments by "new" (instead of "best" or "top").
[link] [comments]
I designed a CH32V003 Compute Module
 | Hi that's a CH32V003 Compute Module i design some time ago, nice specs with 48 MHz clock and tiny for a 2k flash product; Regard Jean-François [link] [comments] |
I just had to check Gemini AI to see whether it was as 'good' as the rest at electronics.
 | Yep! Here's a low voltage DC to low voltage AC inverter courtesy of Gemini: [link] [comments] |






